Home Lab - VMs Communication
Toc-Toc, it’s reachability time!
Prerequisites
- Proxmox node up & running
- OPNsense VM up & running
- 2 Linux VMs up & running
- VM_1
- Name: PIPPO
- IP Address: 172.16.11.10/24
- Gateway: 172.16.11.254 [OPNsense sub-if]
- VLAN ID: 11
- VM_2
- Name: PLUTO
- IP Address: 172.16.12.10/24
- Gateway: 172.16.12.254 [OPNsense sub-if]
- VLAN ID: 12
- VM_1
I’ll skip the Linux Server installation process, you can easily find tons of guide on internet about it.
Lab scenario overview
As per infrastructure design, all the VMs will have the default gateway located into OPNsense VM.
OPNsense has 2 vNIC: WAN and LAN
In the LAN side I decided to configure several sub-interfaces, 1 per each VLAN.
In this example I’ll configure just 2 sub-interfaces, related to VLAN 11 and VLAN 12, in order to allow traffic from PIPPO to PLUTO.
Moreover, I’ll add the firewall rules to allow ICMP traffic.
Important note about VM network configuration
In the previous post I created a Linux Bridge on PVE called “trunk” and I enabled the “VLAN aware” option on it.
This bridge will be assigned to all the Virtual Machines in my environment and I will then associated a specific VLAN to them. I could have also created X bridge where X is the number of VLANs needed, but it’ll make more complex the OPNsense configuration.
So, every VM will has at least one vNIC and it will be associated to the “trunk” bridge, then I’ll add a VLAN TAG ID in the network configuration setting of the VM. Here is an example:
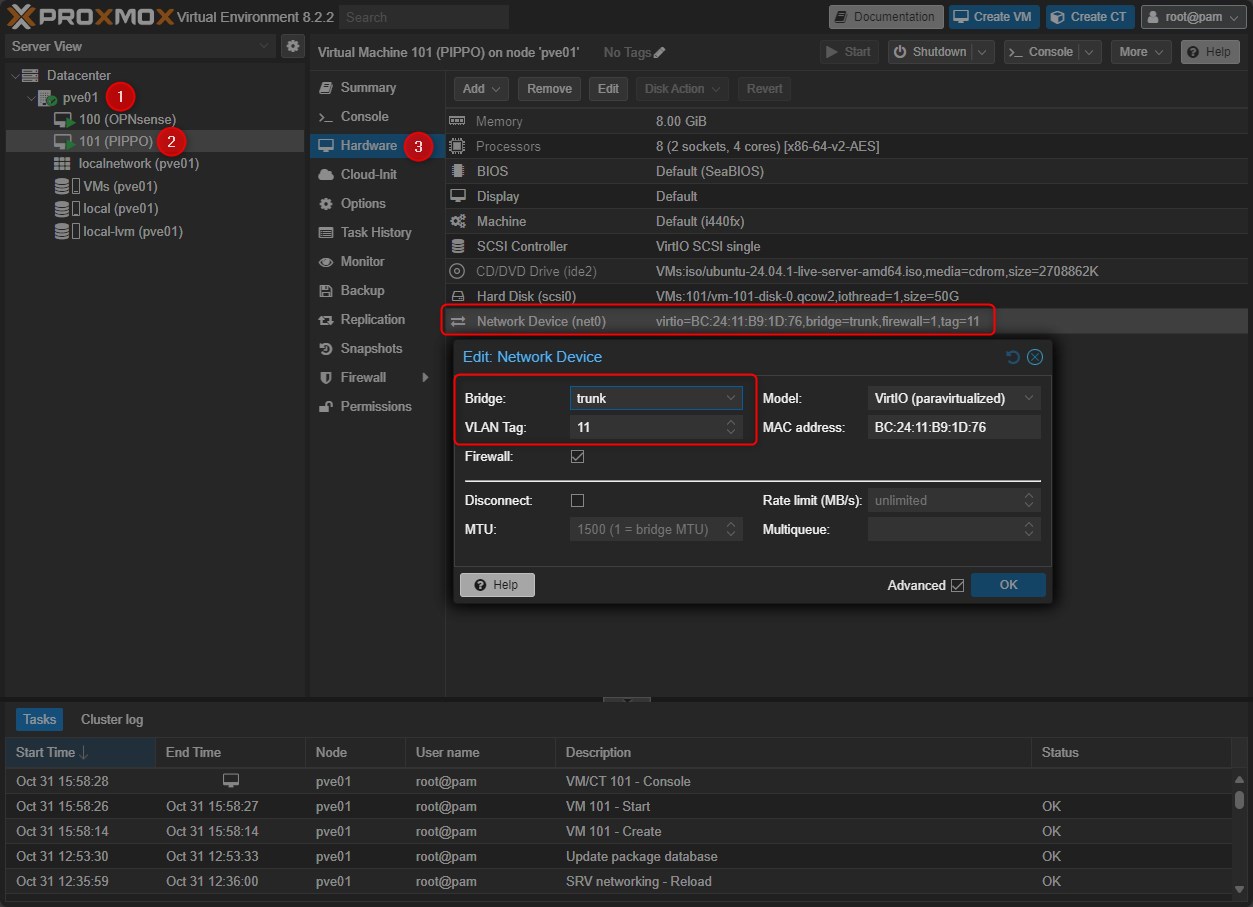
By doing this I can keep OPNsense configuration easy (only 2 vNIC: WAN and LAN) and segment the traffic by using VLANs.
OPNsense sub-interfaces
-
Go to Interfaces > Assignments
Add the “vtnet1” interface as LAN interface. It permits us to configure sub-interfaces and enabled them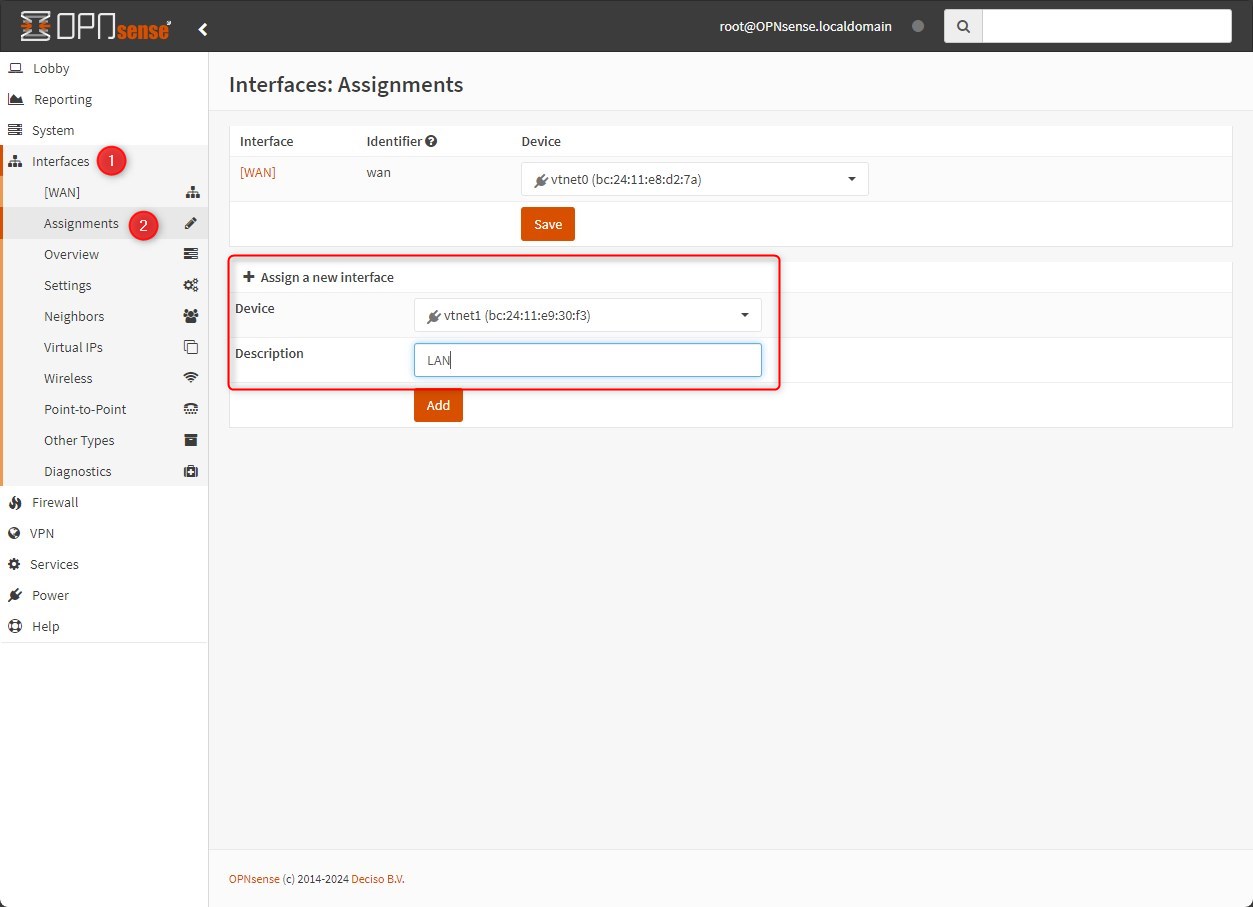
-
Go to Interfaces > Other Types > VLAN
Click on “+” button and proceed with the VLAN creation, here are the required parameters:- Device: Name of the interface, must begin with “vlan0.”
- Parent: Choose vtnet1 (or your LAN interface)
- VLAN tag: The VLAN ID
- VLAN Priority: I’ll leave the default value
- Description: A description
Then, click save and do the same for all your sub-interfaces.
When you created all the sub-interfaces, select “Apply” to finish the configuration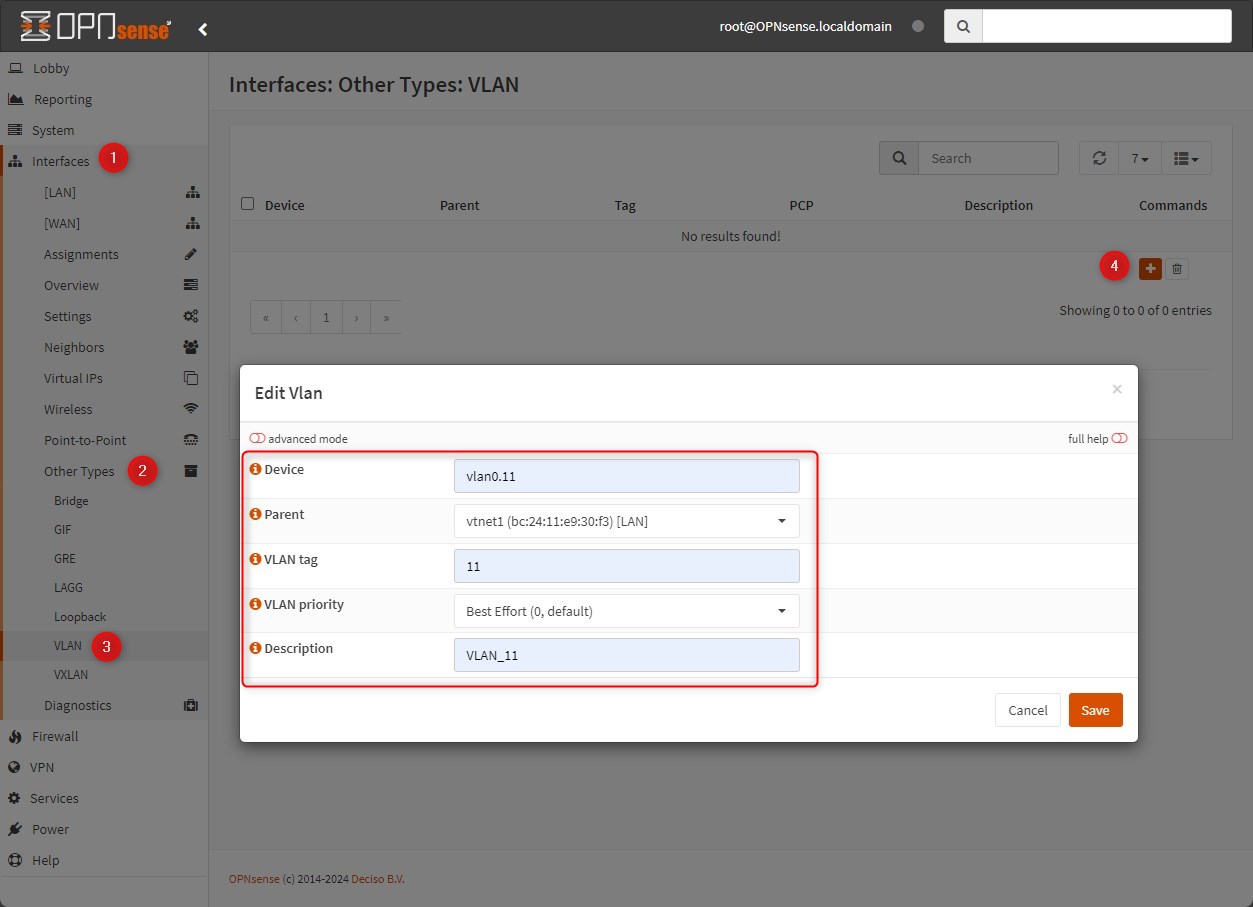
-
Go to Interfaces > Assignments
Add the “vlan0.11” and “vlan0.12” interfaces and select “Save”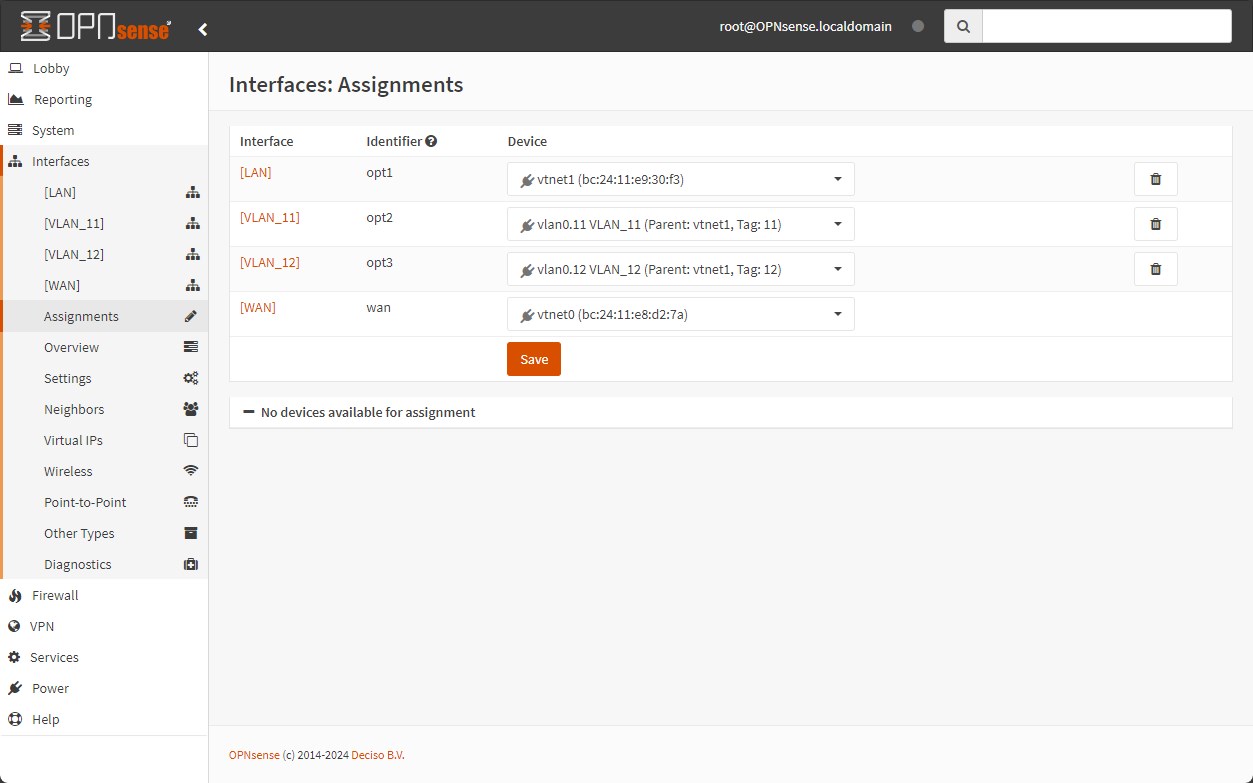
-
Go to Interfaces > VLAN_11
Enable the interface and assign a static IPv4 Address, click on “Save” and then “Apply Changes”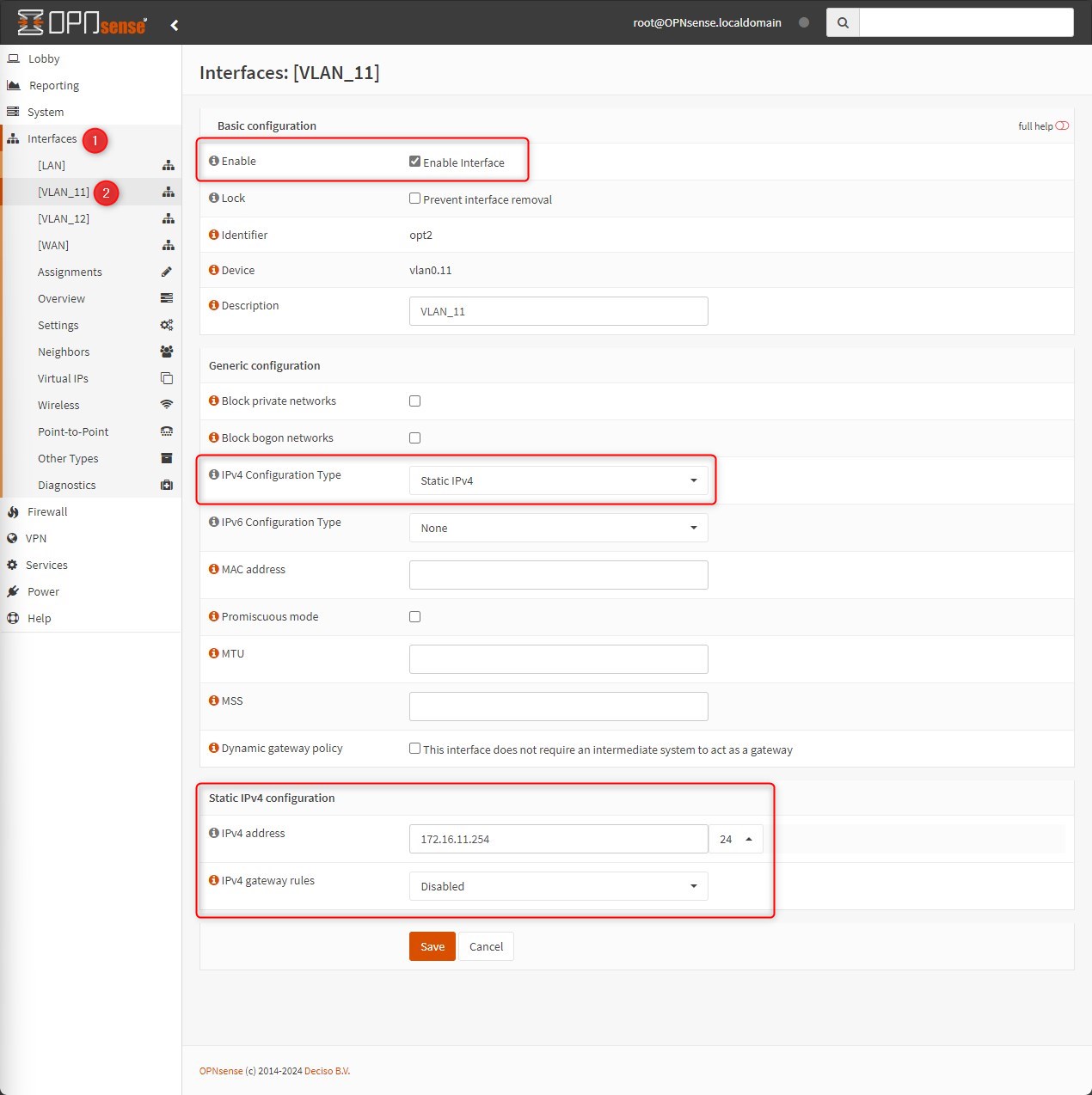
Do the same for each VLAN interfaces
VM reachability - Part 1
Now, let’s test the gateway reachability from VM PIPPO and PLUTO to their gateways.
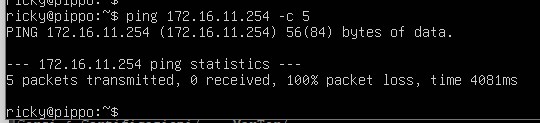
Ping from PIPPO [172.16.11.10] to 172.16.11.254 –> FAIL
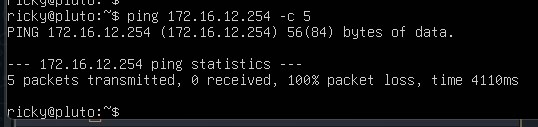
Ping from PLUTO [172.16.12.10] to 172.16.12.254 –> FAIL
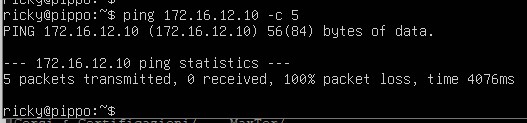
Ping from PIPPO [172.16.11.10] to PLUTO [172.16.12.10] –> FAIL
Why all the test failed? Well, our “router” is technically a firewall, so we must add the policies and rules to allow traffic from one interface to another, let’s do it!
OPNsense firewall rules
I’ll create some rules in order to allow just ICMP between interfaces:
-
Go to: Firewall > Rules > VLAN_11
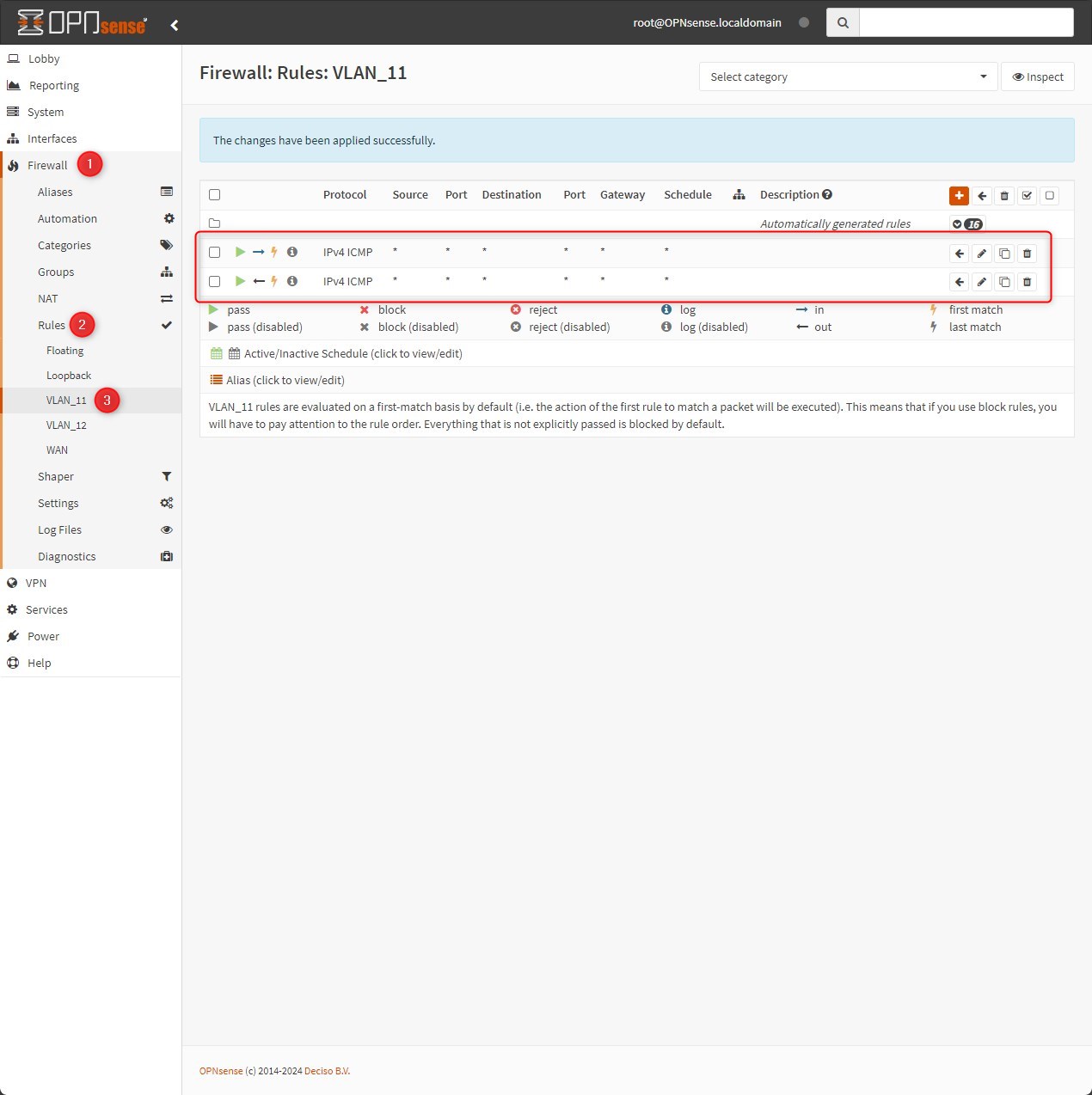
Add two rules, to allow ICMP on both directions “in” and “out”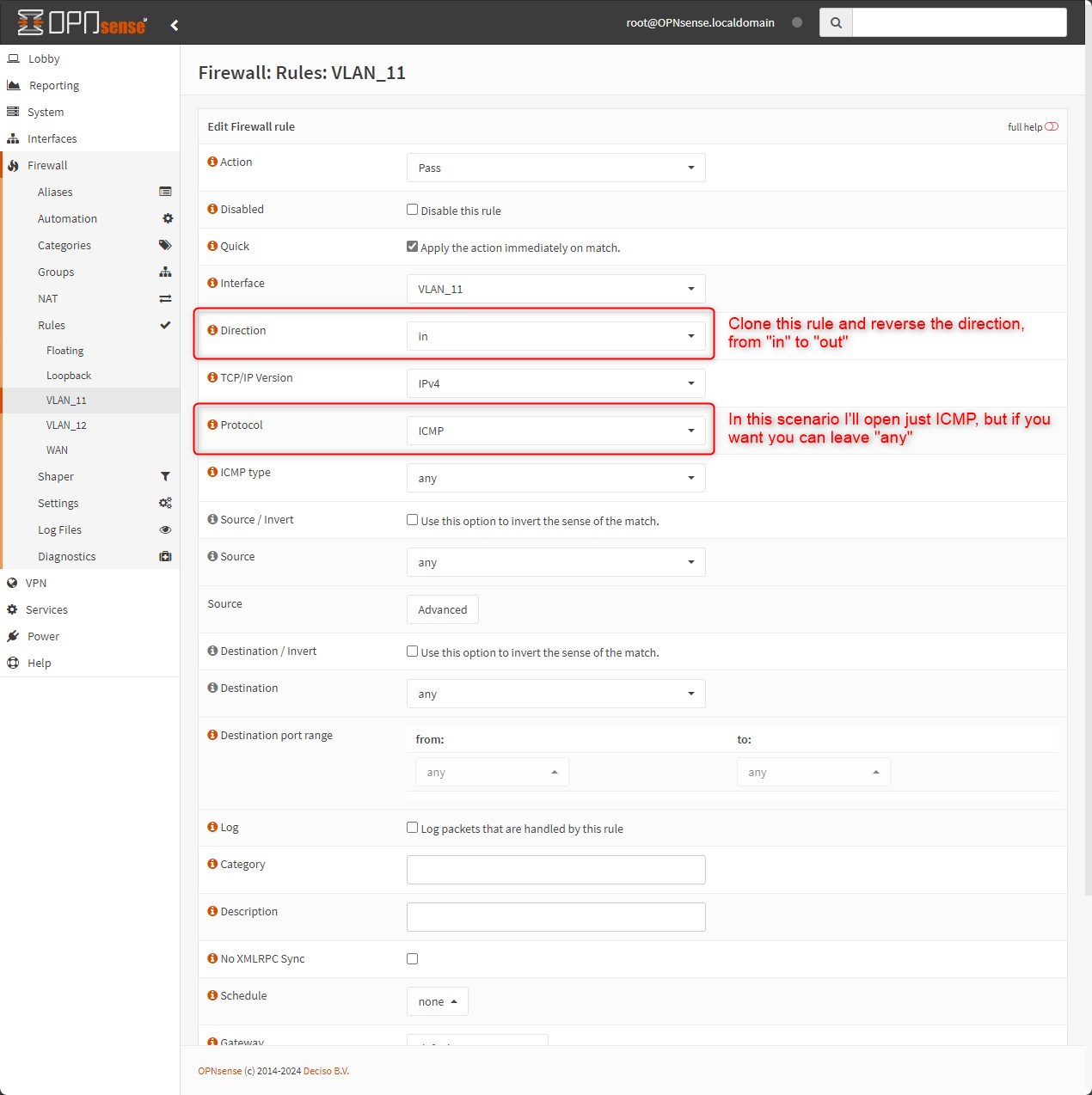
-
Do the previous task also for “VLAN_12” –> Firewall > Rules > VLAN_12
VM reachability - Part 2
Let’s test again the gateway reachability from VM PIPPO and PLUTO to their gateways
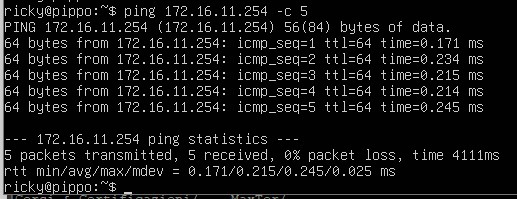
Ping from PIPPO [172.16.11.10] to 172.16.11.254 –> OK
Ping from PLUTO [172.16.12.10] to 172.16.12.254 –> OK
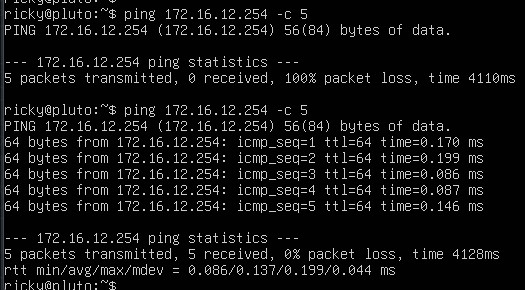
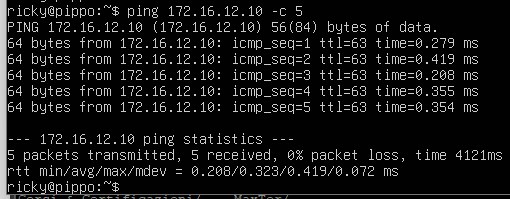
Ping from PIPPO [172.16.11.10] to PLUTO [172.16.12.10] –> OK
That’s all!
Now I’ll proceed with my HomeLab setup and scale the configuration for all the VLANs and VMs that I want.
I really hope you enjoy this series about HomeLab and please, share with me your experience with OPNsense, Proxmox, HomeLab and all the cool stuff you’re doing at home or office!
Thanks for your time I hope that you’re enjoying my blog!
If you have some questions, please drop me a message through social networks!😊
👈 You can find the relative icons here on the left of the page
Riccardo