Home Lab - OPNsense Installation
In this post I would like to show you how to install a OPNsense into Proxmox Virtual Environment (PVE) node!
Prerequisites
The Prerequisites are:
- Proxmox installed
- Disks, CPU and RAM available
- Download the ISO
- Upload the ISO into Proxmox ISO folder
Virtual Machine Creation
Let’s start by creating the Virtual Machine:
-
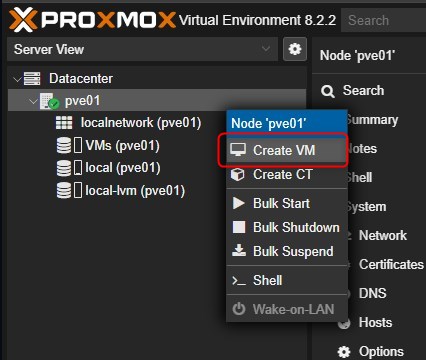
Go to Datacenter > pve01 > Right Click and choose “Create VM”
-
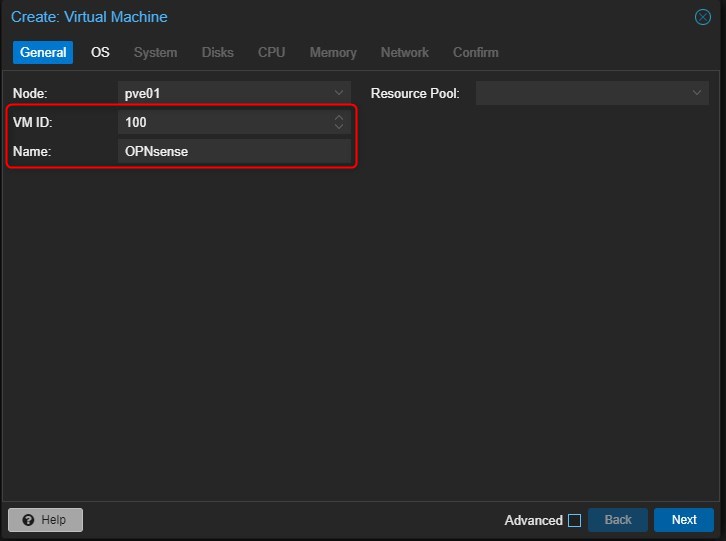
Choose VM Name and ID (it’s a Proxmox identifier, I’ll leave the default one that is the first ID available starting from 100. So the first VM is 100, the second one will be 101 and so on)
-
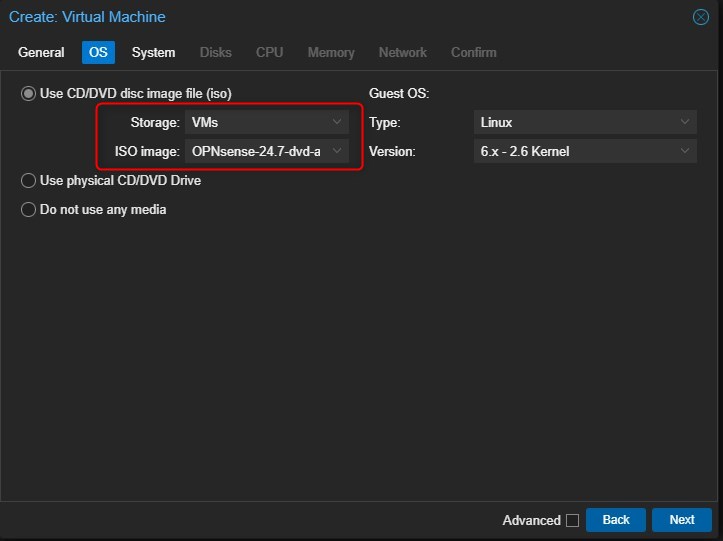
Choose the ISO image. If you can’t see any ISO, please add the OPNsense ISO to the Storage where you want to store ISO images.
-
Leave the default settings on the “System” tab
-
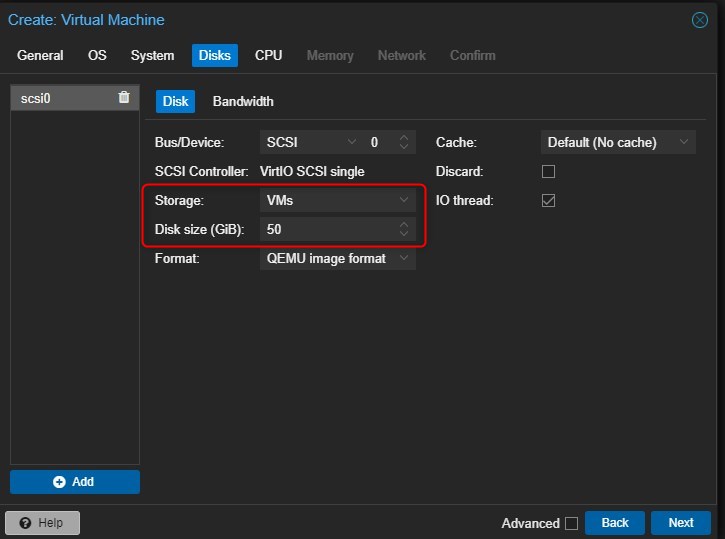
Choose the size of the disk, I’ll put 50 as Disk Size and leave the “Storage” option the default one, that is the same location where the ISO is stored. For me this is the 2TB disk
-
Choose how many CPUs assign to the VM, personally I’ll assign 4 Core and 2 Sockets (total 8 cores) as my physical server has 2 physical processors
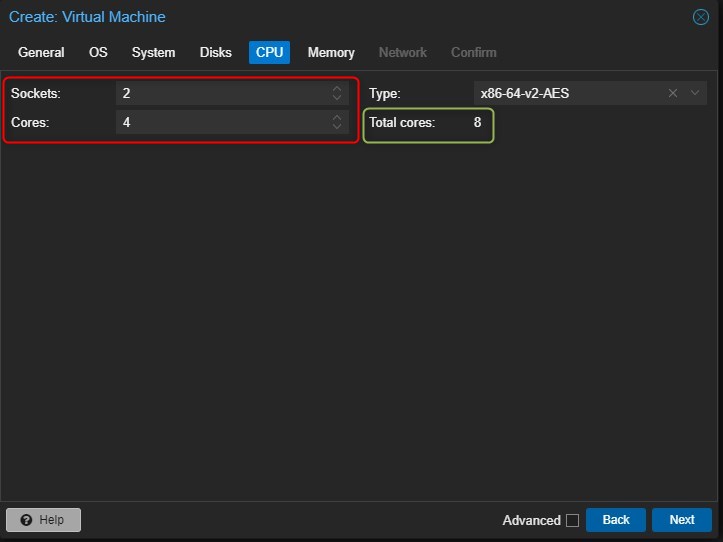
-
Assign the RAM. I’m going to assign 8GB of RAM
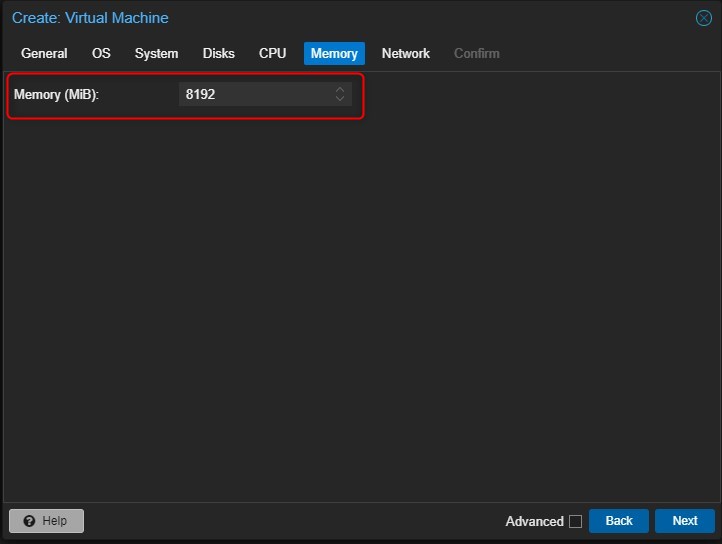
-
Choose the Bridge to assign to this VM. Start with assigning just 1 network interface, that is the default one called “vmbr0” in my Environment. This NIC is logically connected to one of the physical network cards of the physical server.
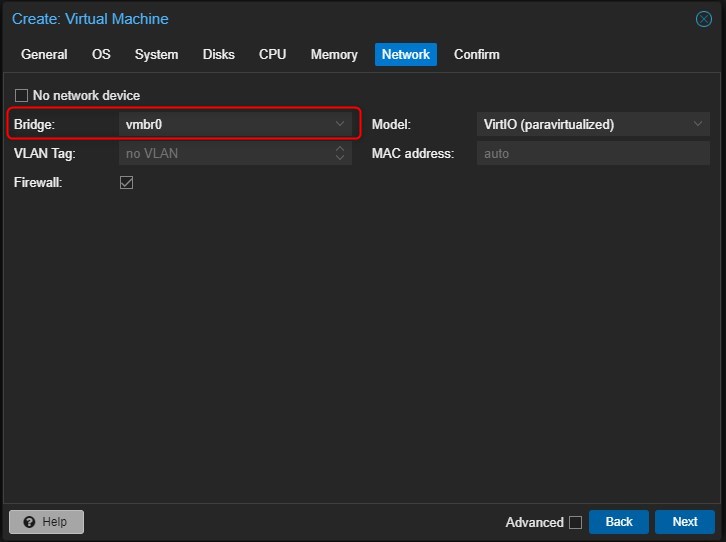
-
Review all the settings and then click “Finish”. Do not flag start VM in this moment
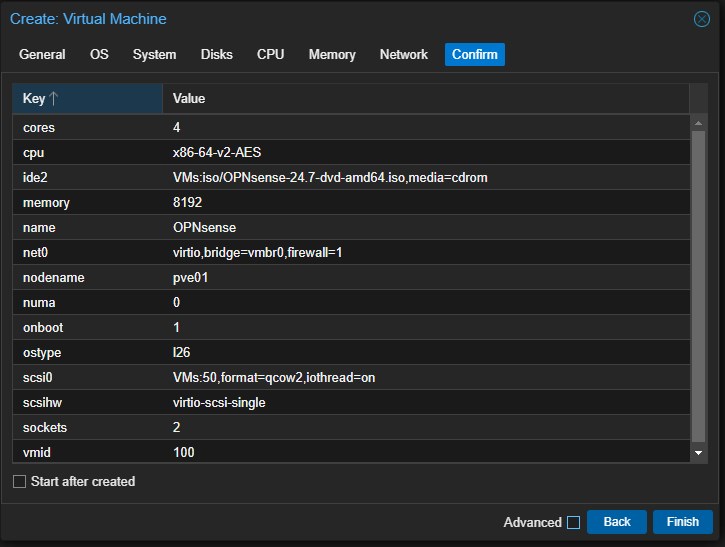
Now that you successfully created the VM, I’ll add a network adapter to it in order to have 2 NICs: WAN and LAN.
The WAN NIC is associated to the default Linux Bridge created by Proxmox during the setup. I want to assign to this interface the IP address 172.16.0.254/24 in order to communicate with the default router of the lab infrastructure.
The LAN interface will be associated to a new Linux Bridge, created by me in the networking section of the PVE node. This bridge will not be binded to any physical server NIC but it will be just a logical segment in my environment. In this bridge I’ll enable the “VLAN Aware” option, because as I show you in my previous posts the lab environment will be segmented in several VLANs.
This bridge will be assigned to all the Virtual Machines in my environment and I will then associated a specific VLAN to them. I could have also created X bridge where X is the number of VLANs needed, but it’ll make more complex the OPNsense configuration
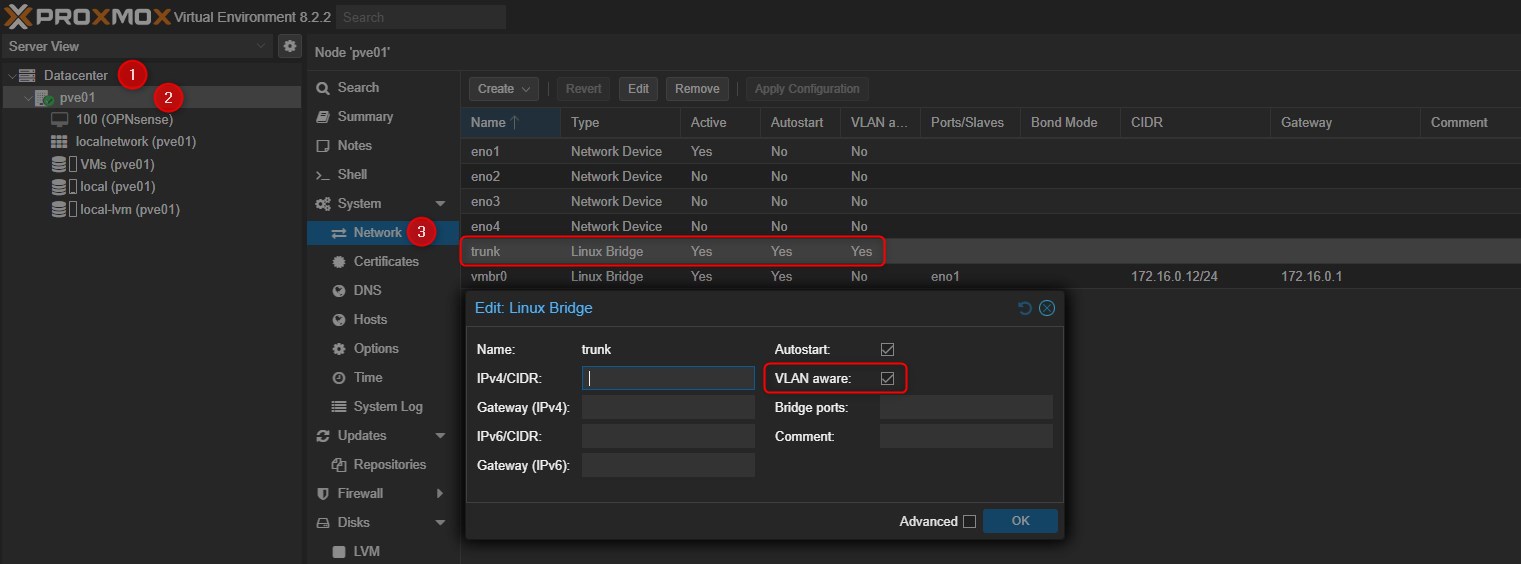
Now that you have your bridge created, just add a new Network Card to the OPNsense VM.
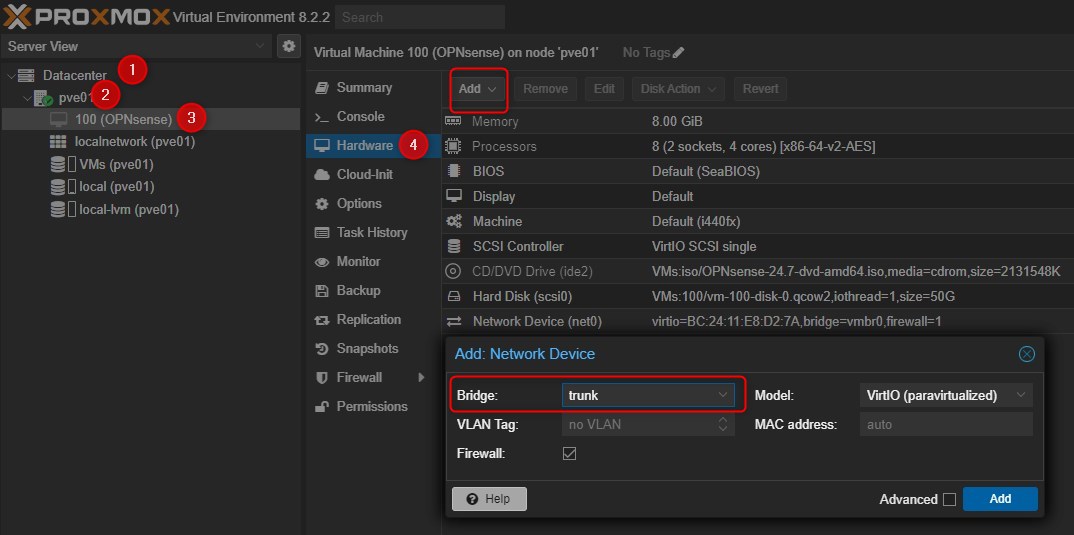
Perfect, this should be the VM configuration:
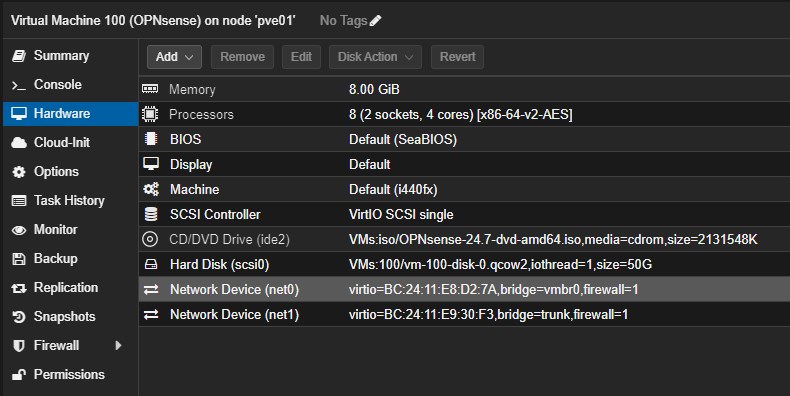
OPNsense VM Deployment
Now that we have created our VM, we can proceed in configuring it!
-
Power it on and lunch console
-
The system will boot and at some point you will read “Press any key to start the manual interface assignment”, when you see it, press any key to start the interface assignment:
In this phase we’ll create just two interfaces: WAN and LAN. The VLANs will be created later via GUI.
-
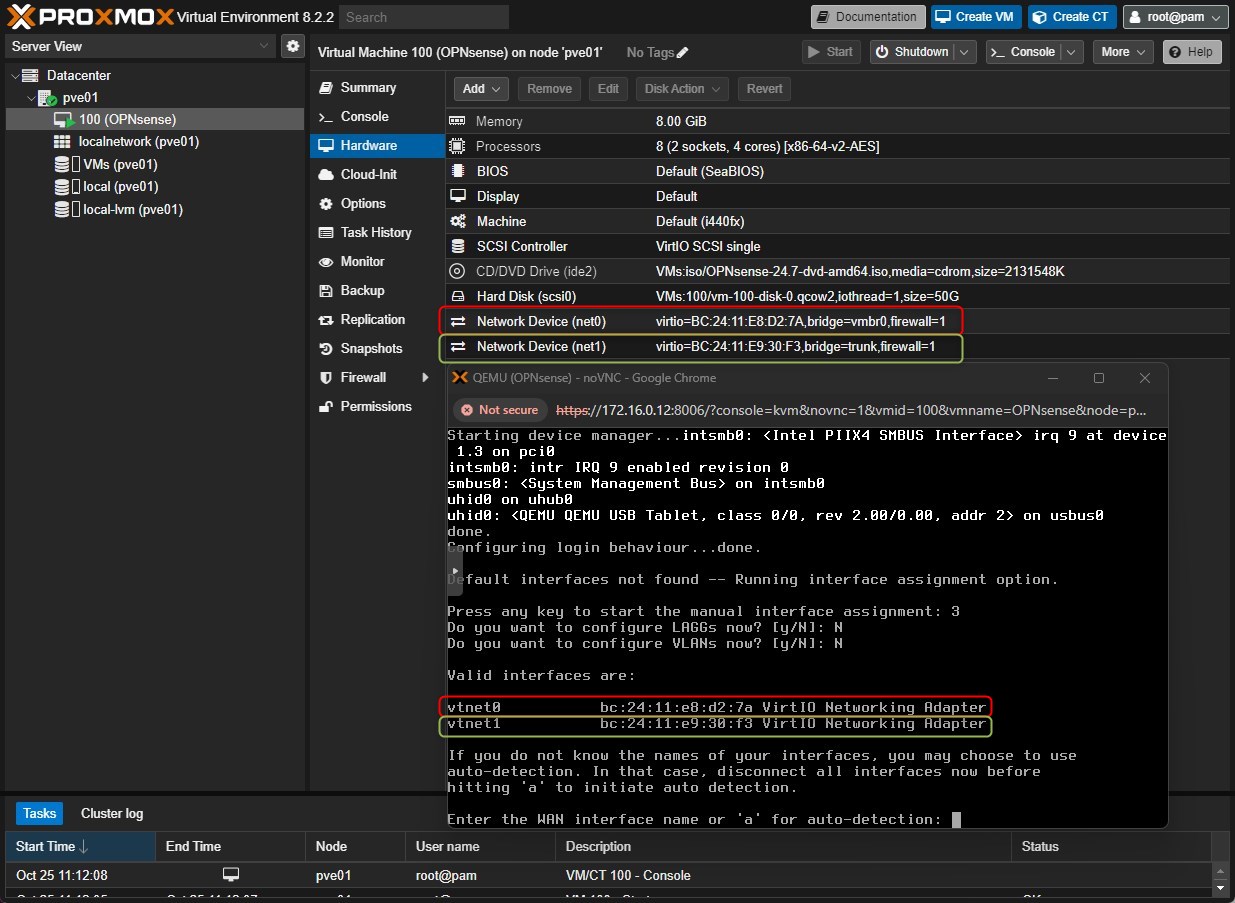
Go back to PVE node and go to the hardware section of the VM, we need to check the Network adapters MAC addresses.
In my environment the MAC addresses are:- WAN: BC:24:11:E8:D2:7A (red lines)
- LAN: BC:24:11:E9:30:F3 (green lines)
-
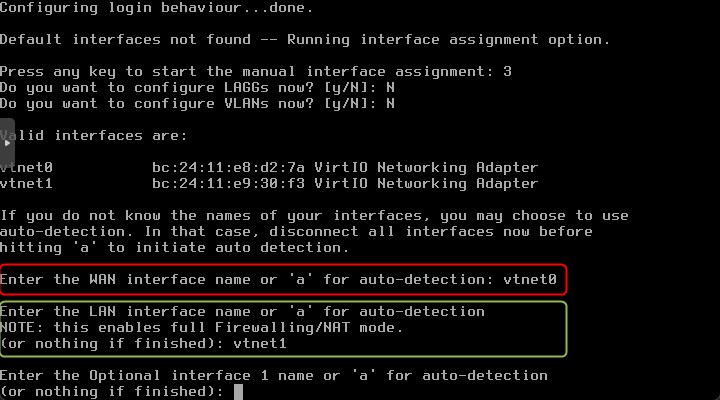
Enter the WAN interface. In my environment is the “vtnet0” interface
-
Enter the LAN interface. In my environment is the “vtnet1” interface
-
Review the configuration and type “y”
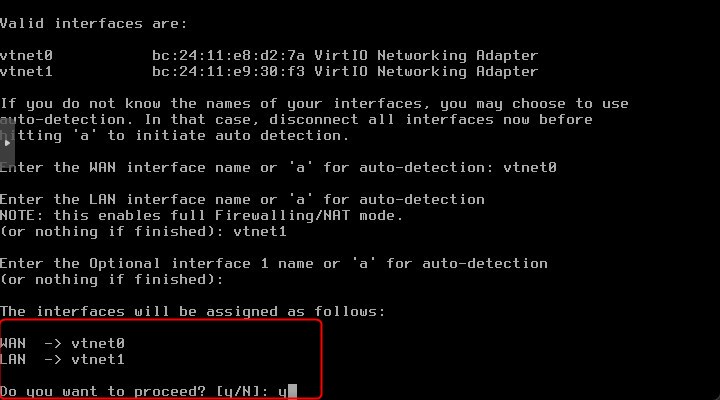
Now the OPNsense will complete the boot process and if you have a DHCP server on your WAN side, you sould be able to see that the WAN interface has obtained an IP address.
When completed, you will ask for a username and password login. Here we have two options:
- Login as “root” and continue in live mode (no permanent installation)
- Login as “installer” and proceed with a permanent installation
-
Login as “installer”, here are the credentials (November 2024):
- Username: installer
- Password: opnsense
-
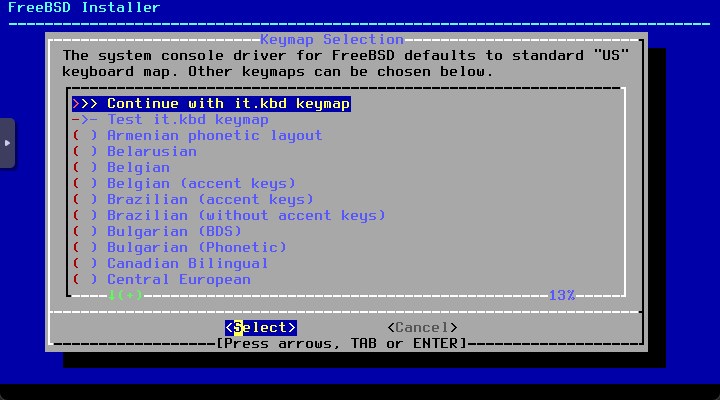
Select the Keymap. I choose Italian
-
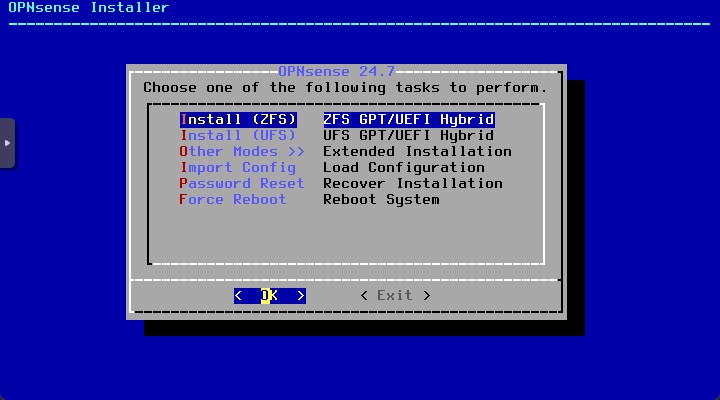
Choose ZFS vs UFS. I choose ZFS
-
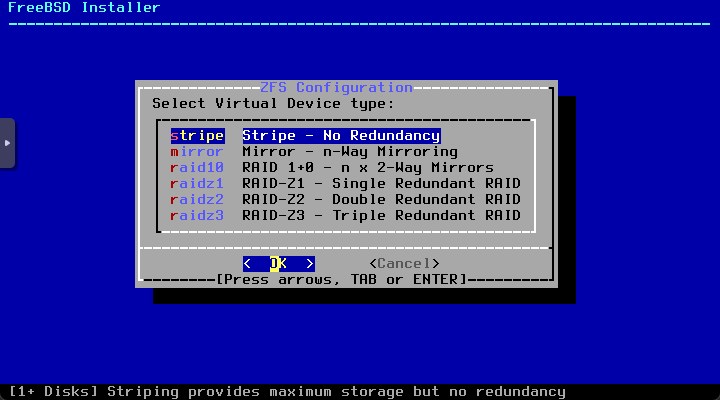
I’ll not configure any RAID so I’ll keep the default ZFS Configuration Settings

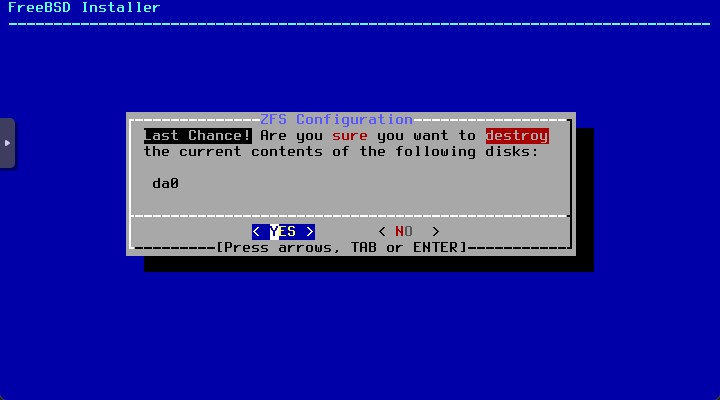
-
The installation will start and you can monitor the installation progress from console
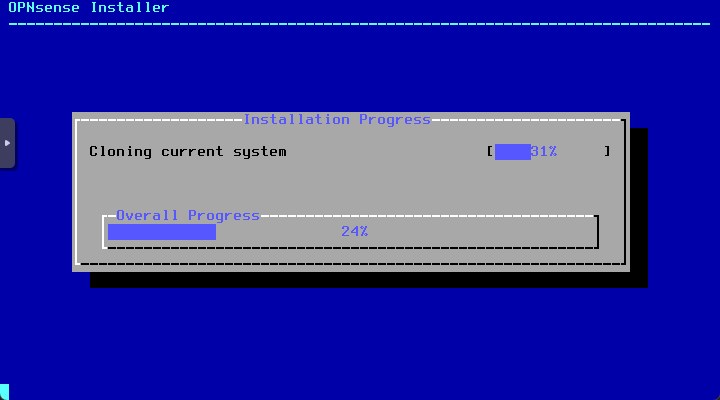
-
Do not change the root password (we’ll change it later during the wizard setup in the GUI) and finish the installation
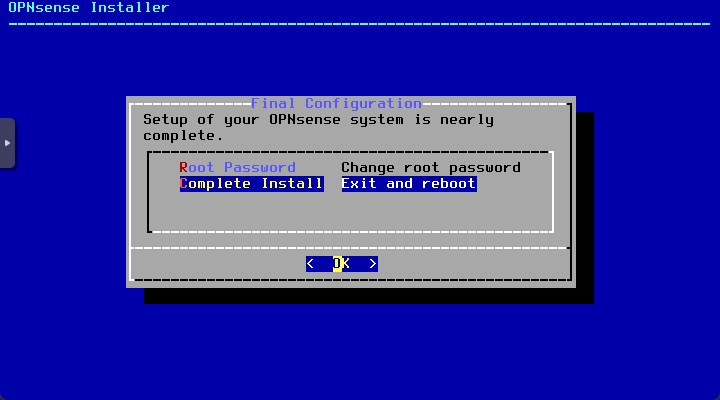
The sysem will reboot. When the boot will be completed, shutdown the VM and remove the CD/DVD Drive from the hardware VM’s setting. Then power it on again.
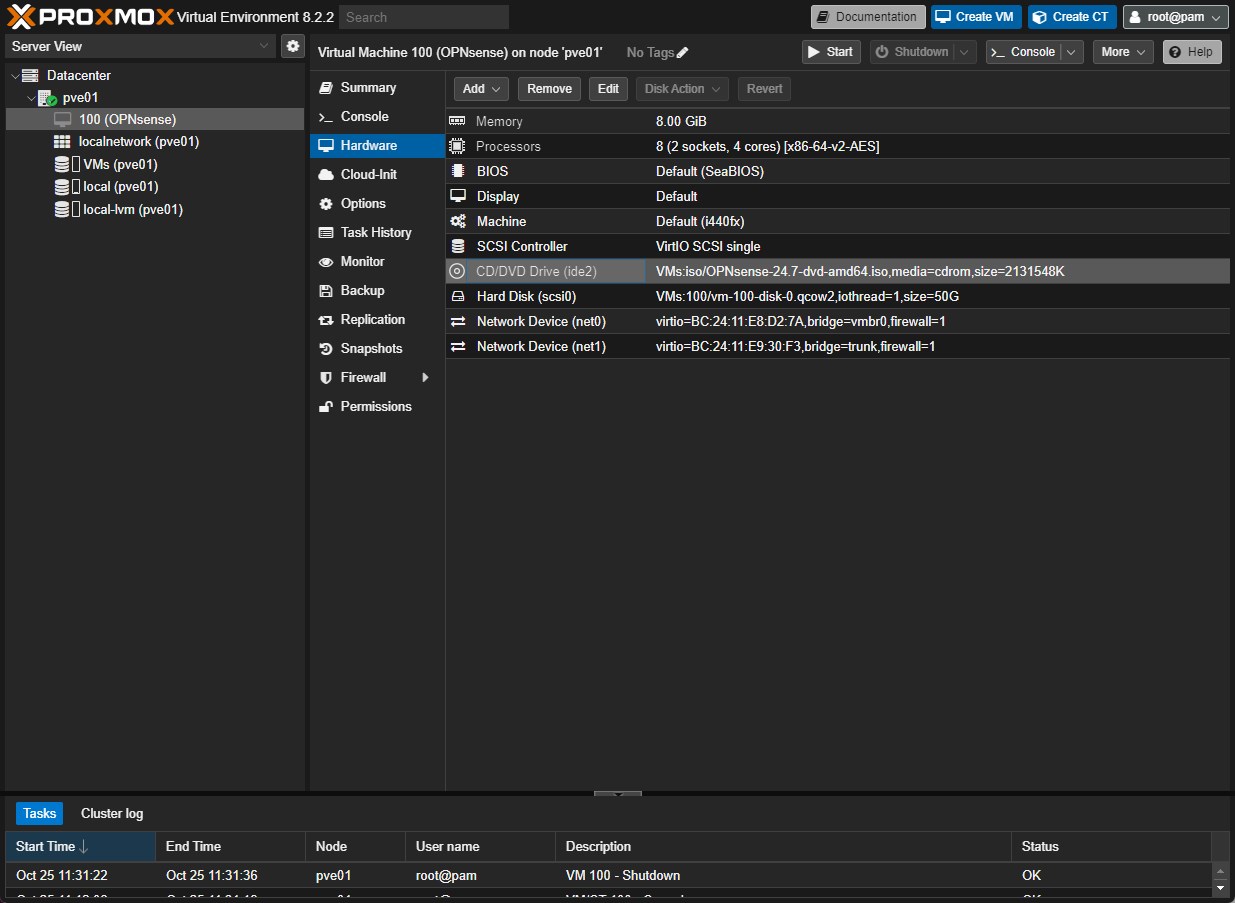
OPNsense VM Setup & Configuration
Now that we have out VM Up & Running, we need to configure it!
I know… you see the IP address on your welcome page in the console and you’re trying to ping/access it but you can’t, right? Let’s fix it!
First of all, proceed in logging in into console with the default credentials:
- Username: root
- Password: opnsense
By default, OPNsense has this console menu where you can choose your option.
To make OPNsense WAN IP Address reachable we need to temporary disable the firewall. As you know the default action in a new firewall is “deny any”, because you must add the correct rules and policies. To do it, let’s press “8” (Shell) and type “pfctl -d":
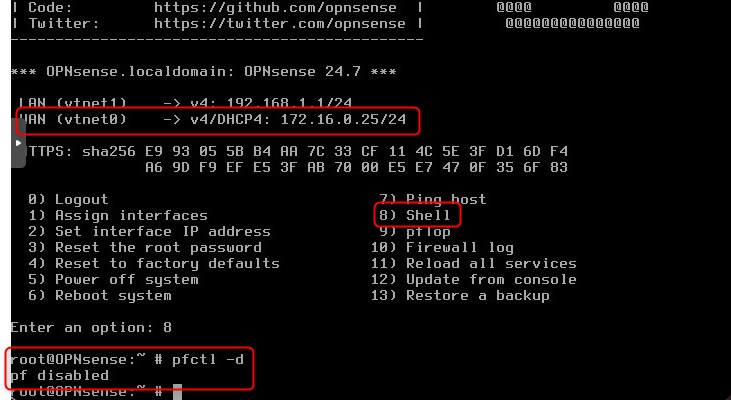
Now, the WAN IP Address should be reachable:
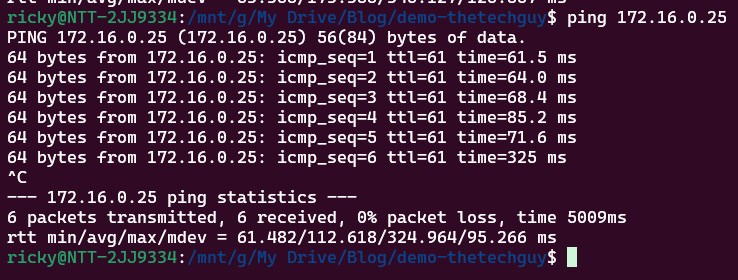
During the entire setup process I strongly recommend you to keep the ping active, and if you see a packet loss please re-apply the “pfctl -d” bash command.
Cool! Now proceed with GUI setup, let’s access the WAN IP via your default browser: https://WAN_IP_Address
Bypass the self-signed certificate and login with the default credentials:
-
Username: root
-
Password: opnsense
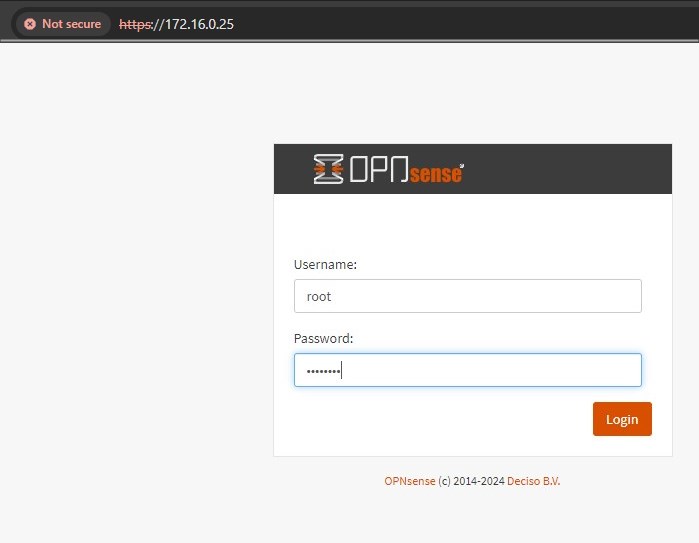
You are now logged into OPNsense firewall! You should be redirect to the Wizard page, where you can complete the setup of the VM
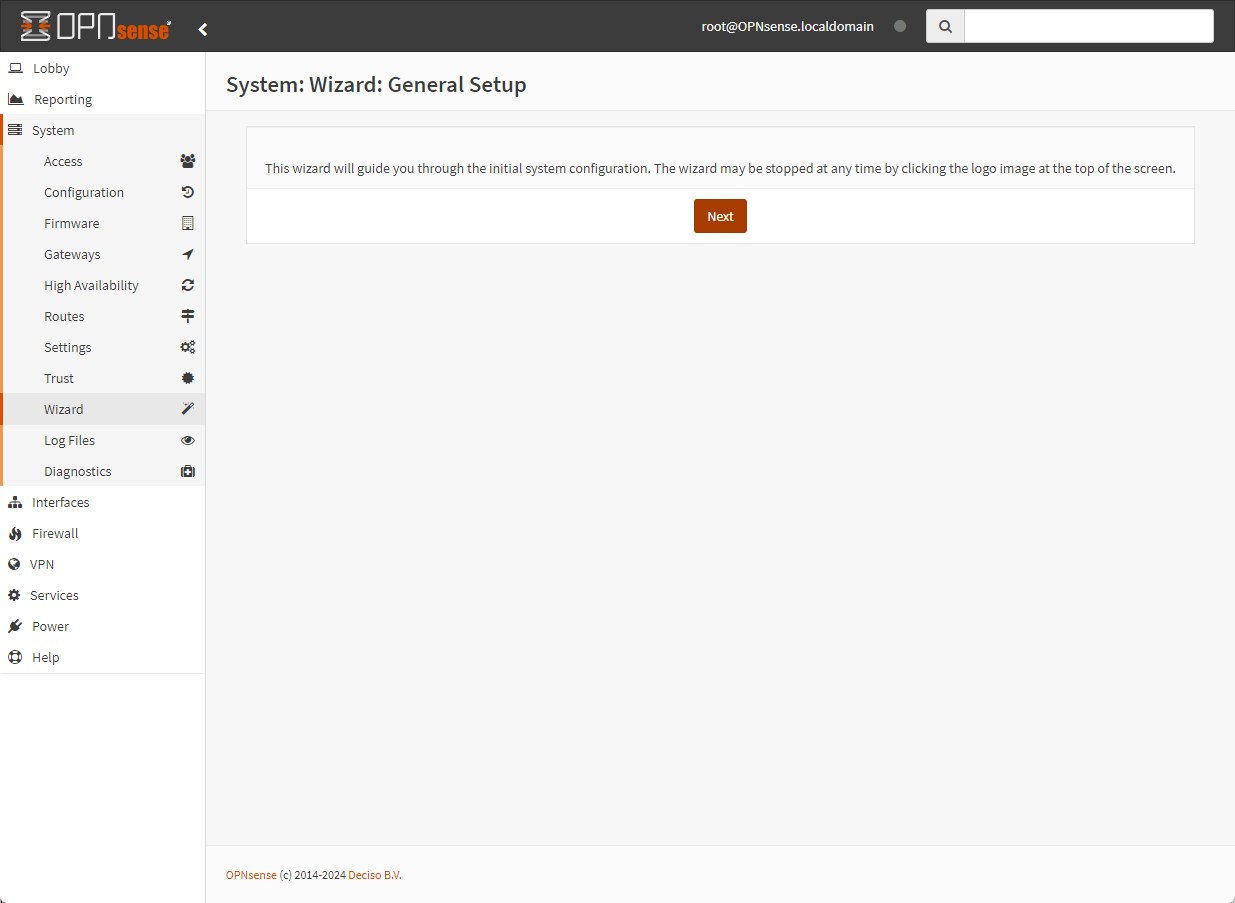
-
General Information: define hostname, domain, language, DNS servers
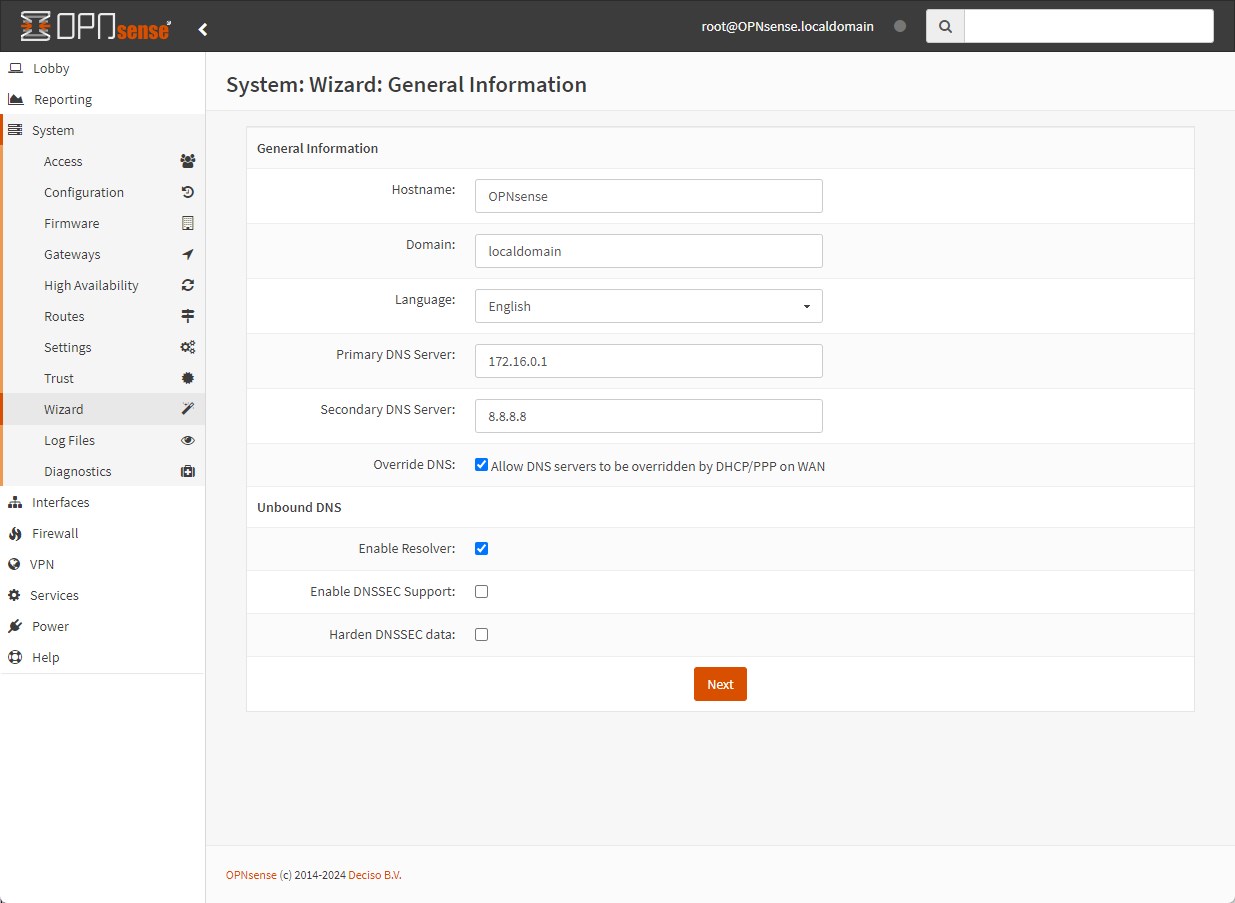
-
Time Server Information: I leave the default ones
-
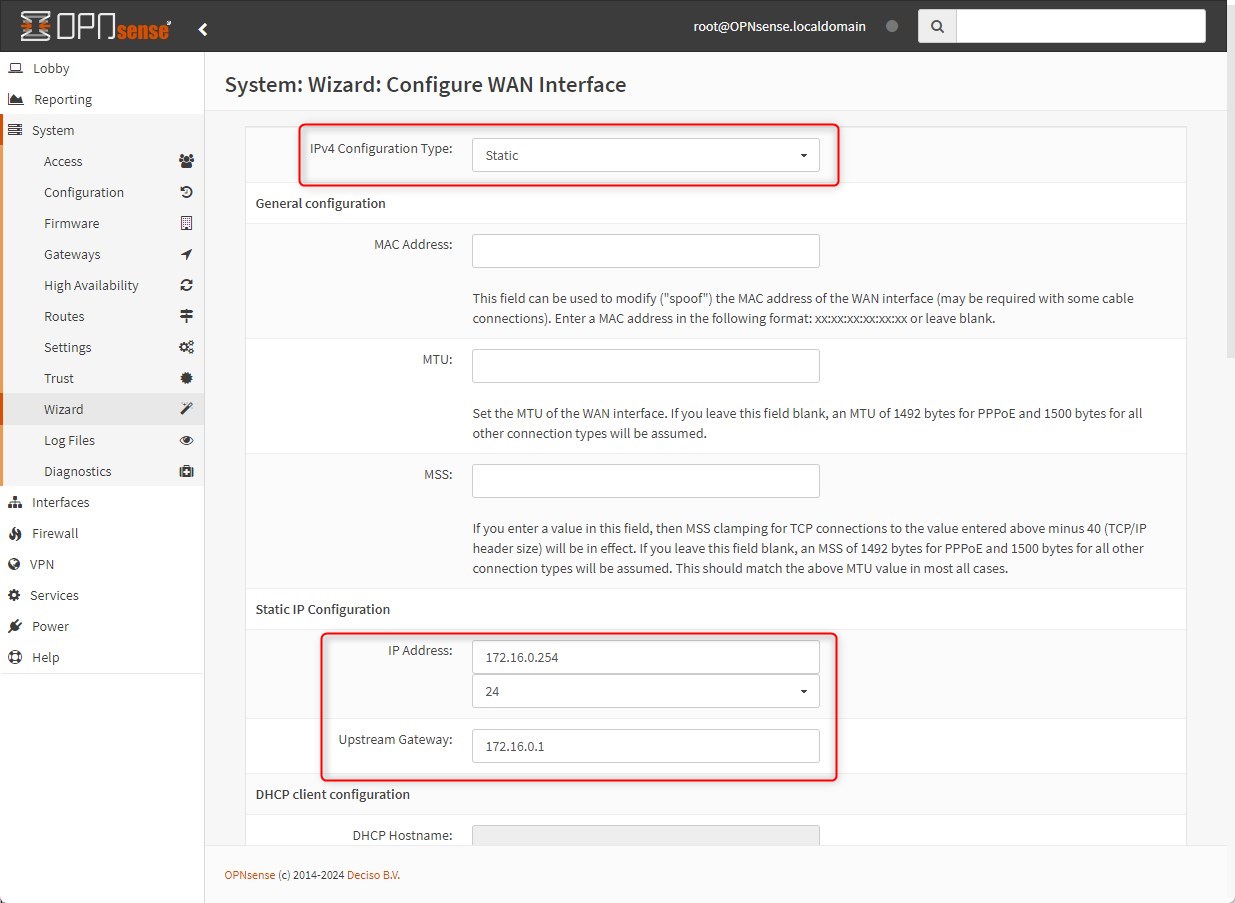
Configure WAN Interface: In my environment it’s important to assigne a static IP address to WAN Interface.
- IP Address: 172.16.0.254
- Mask: /24
- Default Gateway: 172.16.0.1 (LTE Router IP address)
In the same section, and ONLY if you are using a private IP address on your WAN Interface, please disable the following options:
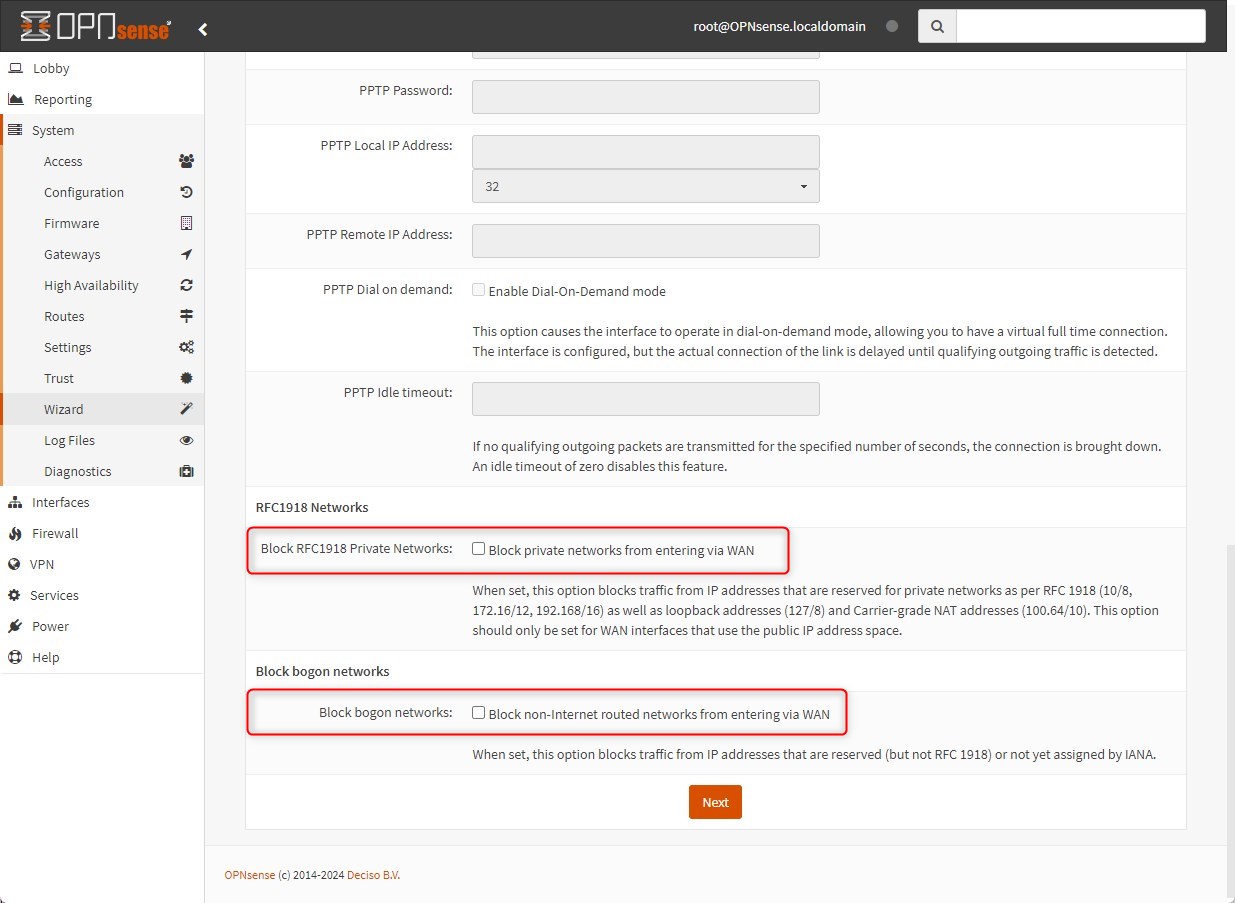
-
Configure LAN Interface: I leave black this because I’ll create several sub-interfaces and I’ll assign them the IP Addresses
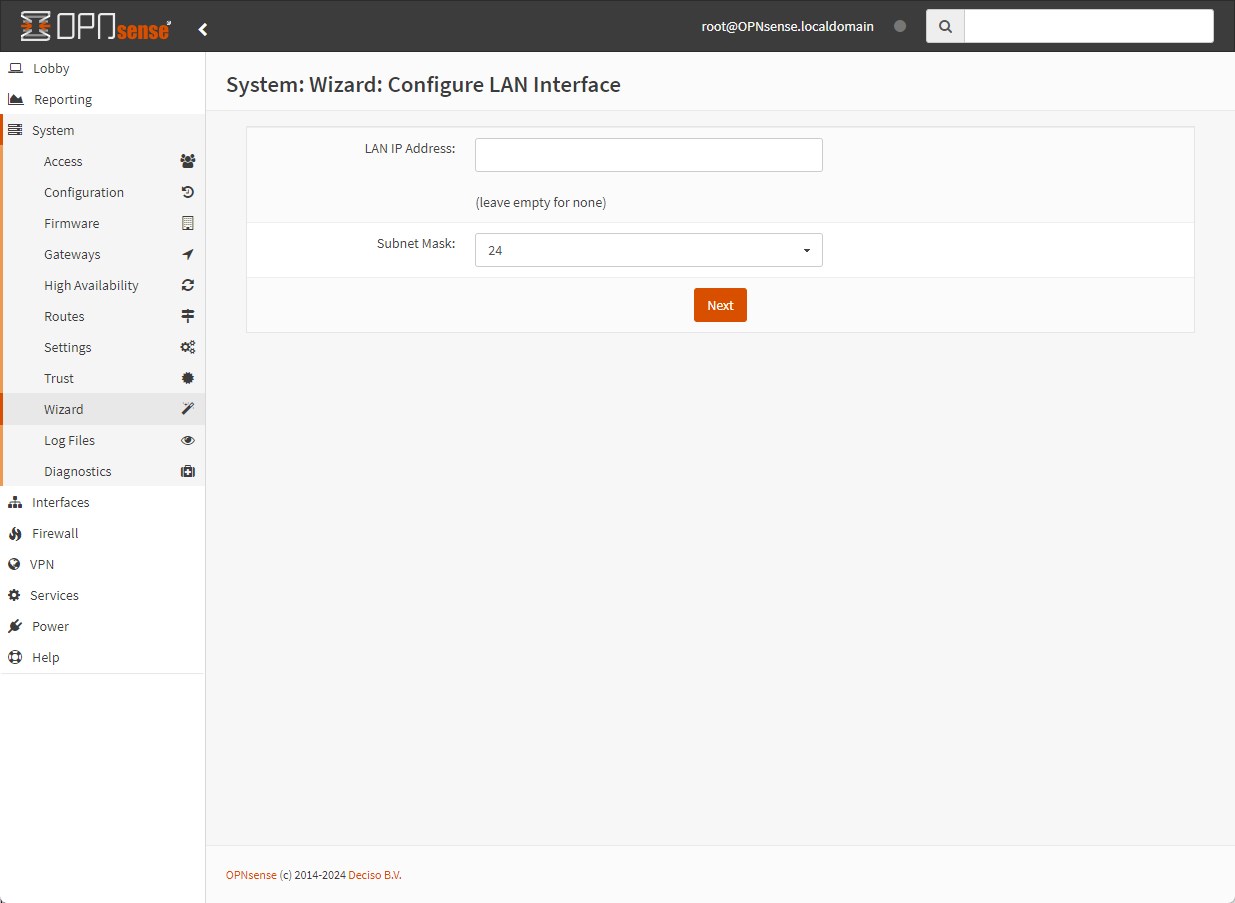
-
Select a root password and finish the installation
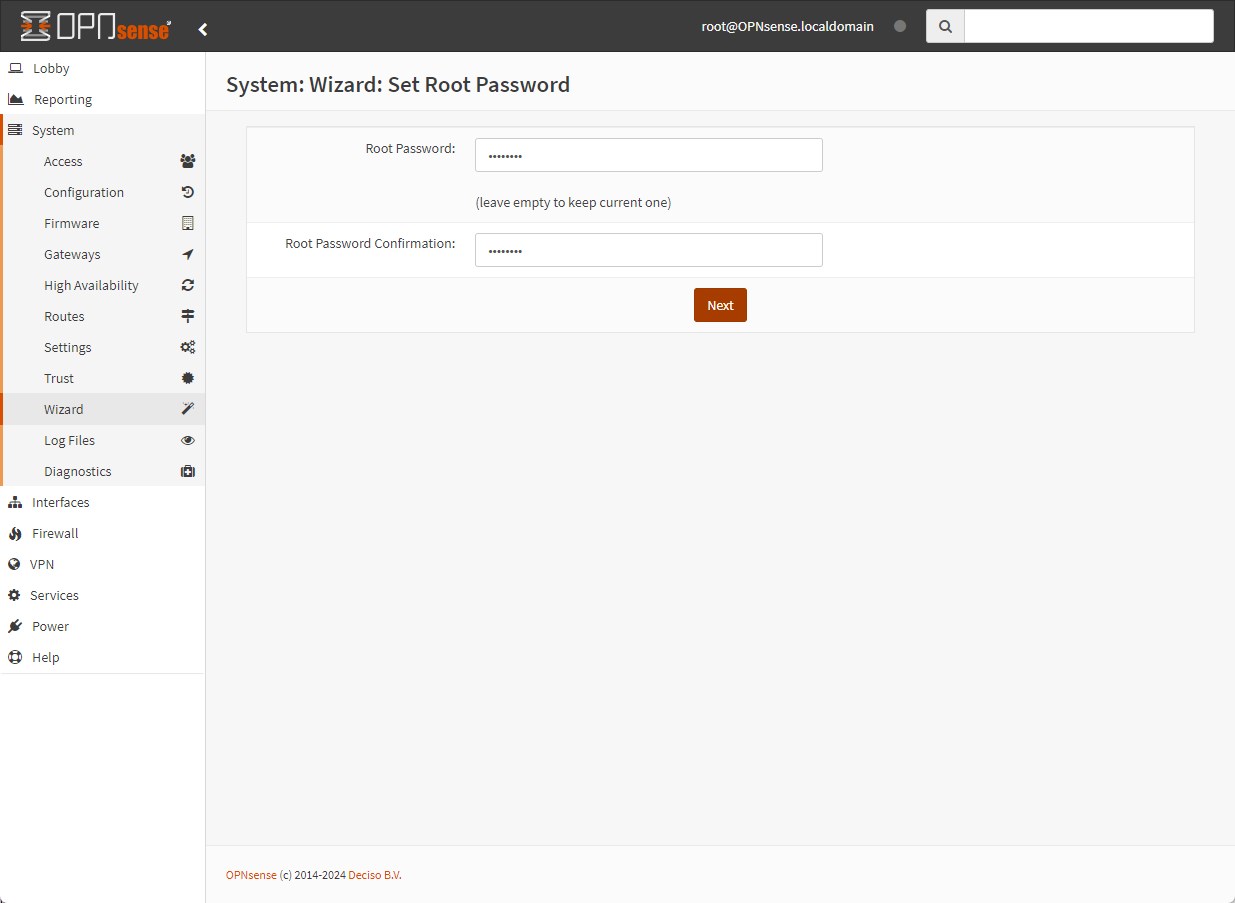
You will no longer be able to ping old WAN IP address neither the new static IP…. Why? Because we do not add any rules to WAN interface to allow ICMP and HTTPS access!
Go back to console and type “pfctl -d”, after that you should be able to ping the new WAN static IP Address.
Then, move to your browser and login to OPNsense with your credentials, you will see something like that:
Let’s move on and add firewall rules.
-
Go to: Firewall > Rules > WAN and create two new rules, one per each direction
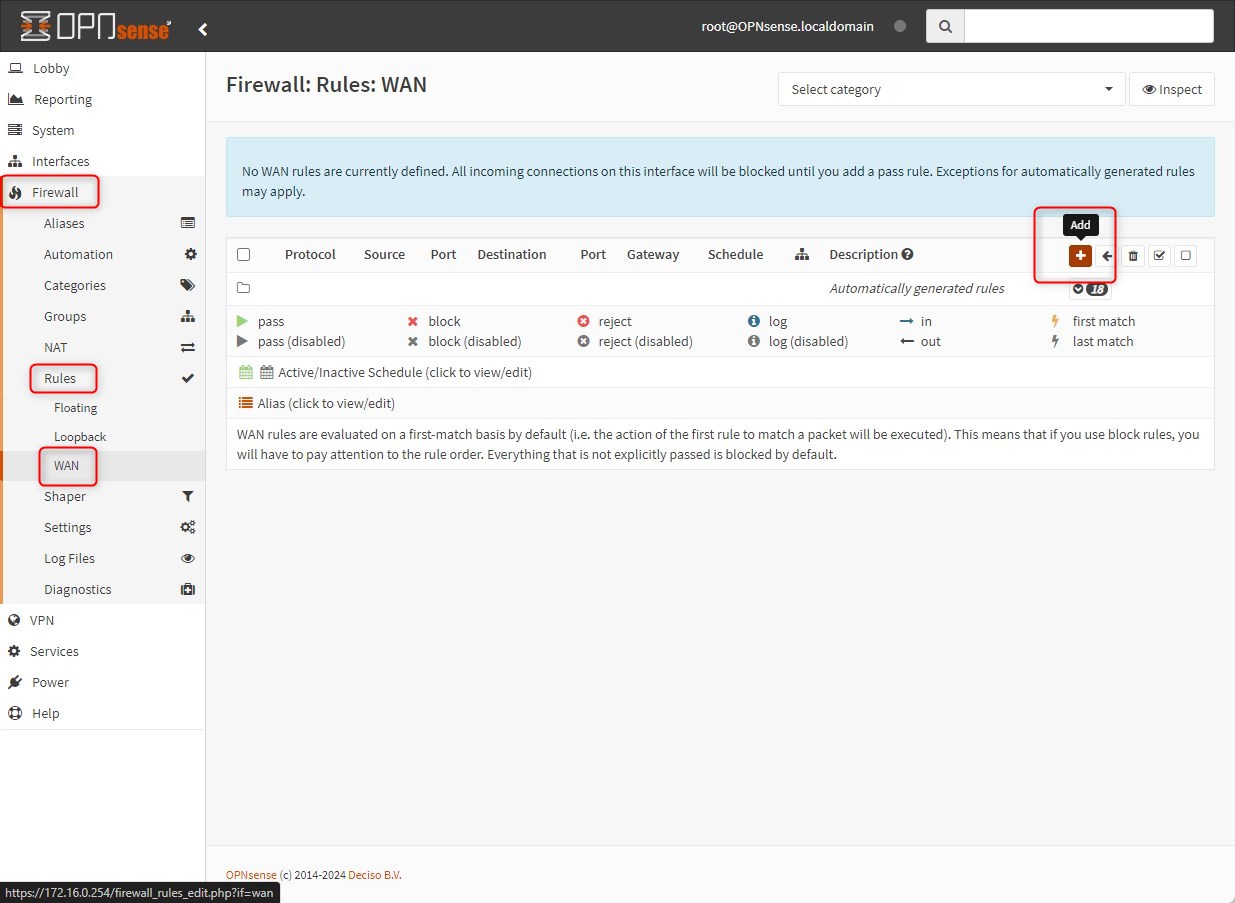
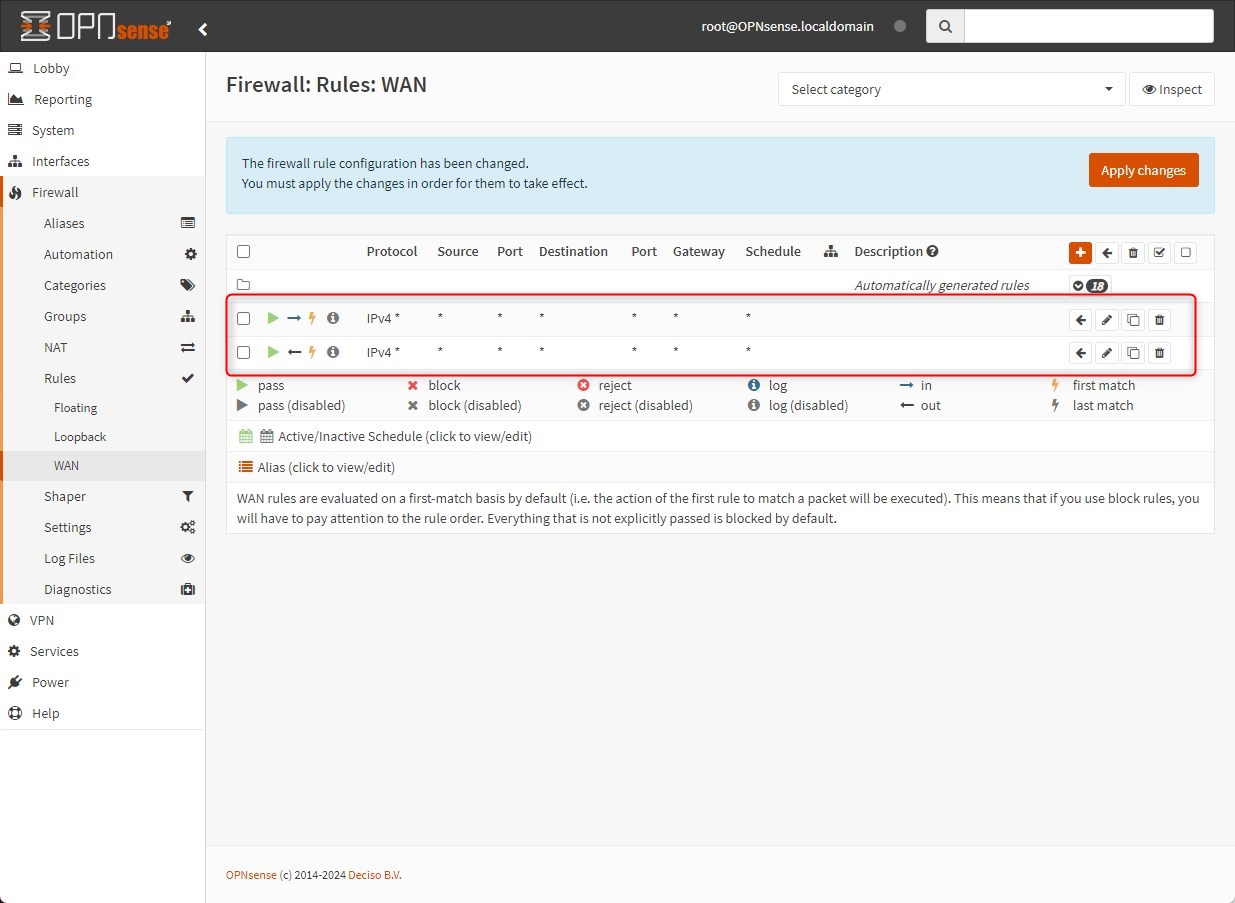
Then, click on “Apply changes”, wait some seconds and if it’s stuck just reload the page.
I know…. it is not a best practice to allow any type of traffic to and from your WAN interface, but we are in a lab environment and it’ll allow me to skip some steps and reduce the number of rules. Moreover it’ll simplify troubleshooting because I’ll not check for any firewall rules that could potentially block traffic, because I allow everything.
Again, it is NOT a best practice and please, do NOT do it in a production environment -
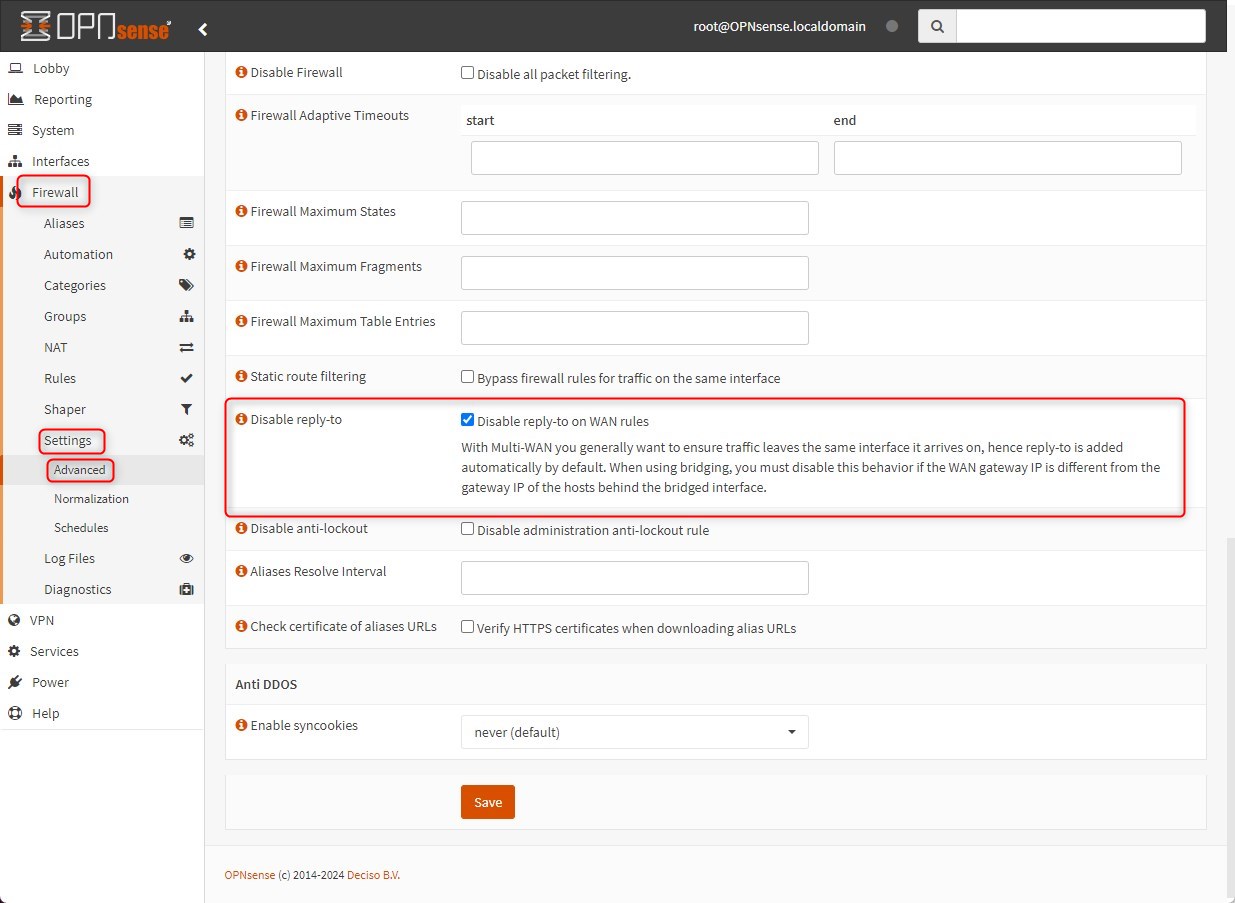
[Optional, based on your setup] Go to: Firewall > Settings > Advanced and select “Disable reply-to on WAN rules” then save the configuration.
Ok guys, now that you have your OPNsense VM deployed and configured with some basic and standard options, we can move one with detailed configurations such as: sub-interfaces, VLANs, IP Addresses, Firewall Rules and much more!
In the next post I’ll configure two sub-interfaces with IP addresses and VLAN tag and I’ll create 2 Linux Server VMs. I’ll assign them two different VLAN ID and I’ll test the connectivity through the OPNsense firewall…. Stay tuned! 😉
Thanks for your time I hope that you’re enjoying my blog!
If you have some questions, please drop me a message through social networks!😊
👈 You can find the relative icons here on the left of the page
Riccardo